Six tips for reducing IT/Security and Compliance costs? In this world? Where cyber-attacks seem to occur dally?
Huh? Could I be that clueless?
If anything, with all this paranoia… companies should be increasing IT/Security budgets, not decreasing them!
Right; this is what happens when the mob mentality becomes the “norm” when planning strategy, especially in the corporate workplace.
Right now “the leader see leader do” mentality in the corporate workplace has beefed up IT/Security budgets to the point we may be creating our own smoke screen for lack of ….IT/Security and/or compliance.
It’s time to re-evaluate the role of IT/Security and Compliance in the corporate workplace today. A smarter, shared leadership approach will foster a more secure environment in compliance while saving internal overhead in the process.
I will say up front IT/Security is not my subject matter expertise. However, efficient delivery is, in parallel with Shared Leadership. When I apply that model, my model and subject matter expertise, I come up with some interesting opportunities.
What exactly is IT/Security and Compliance anyway? I’ve been at fortune ranked companies that actually set aside billions (with a B) in anticipation of fines imposed by regulators for out of compliance practice. So what role does IT/Security and compliance play if the company still budgets billions for out of compliance fines?
I’ve been at fortune ranked companies with strict rules on access; to applications, files, servers and emails based on best practice (or leader see leader do) from other companies. However, these rules don’t apply to everyone and are not always practiced. Therefore, what good are they? If you’re an outsourced vendor; an Authorized Service Provider, these rules may not even apply to you. This means everyone from this vendor has more unrestricted access to your company than you (an officer of the company) do!
Go figure!
I’ve been at fortune ranked companies that have specific deliverables for IT/Security and Compliance throughout the SDLC. However, 99% of the time, those deliverables can basically state no change or no security concerns! Meaningless. Talk to an IT/Security person and they will most likely say something like “you have no idea what’s going on”. Ask them to explain… you get silence!
Meanwhile, systems are hacked daily!
So what can be done to improve this very expensive internal overhead?
The size of the IT/Security and Compliance budget should be scaled back. Do we really need IT/Security spending most of their time reviewing password violations? Do we really need Compliance officers spending most of their time reviewing internal password requirements? Why not redeploy these guy’s internally within the company as developers, project managers, maybe even testers? Something more productive generating more bang for the buck than what’s currently being generated. Especially when you consider even with the beefed up IT/Security, systems are hacked daily.
We need a Shared Leadership approach to IT/Security and compliance. IT/Security and compliance planning and monitoring must be a company-wide effort. EVERY COMPANY will say IT/Security and Compliance is a company-wide effort, but how many have actually implemented these Six recommendations?
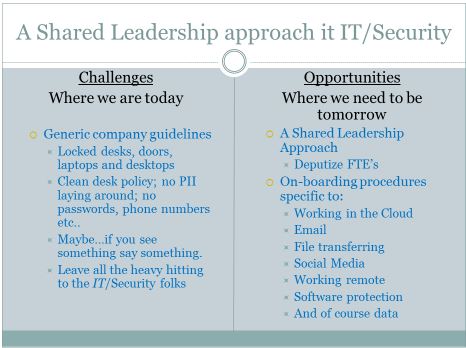
There will always be resistance to change; always. Our companies need us now more than ever but not the “tell me what you want me to do” version. Our companies need courageous change agents. Change Agents that step up and say “based on my subject matter expertise, here’s what I think is needed most next” and then be accountable for those actions.
Building a better workplace starts with you! Are you game?
Charlie Lobosco has over 40 years’ experience in Corporate/IT and lessons learned in over 25 fortune ranked companies. Charlie is a Shared Leadership Expert, Agile Transformation Coach, and Corporate Change Agent.
For more go to Charlieandeva.com
© Copyright 2024 - Charlie and Eva
Designed by : Web Strategy Plus